6.1.2.8. Authenticate (dialplan application)
1. Authenticate - authenticate an user with a dialled pass code
NOTE: This application is valid for Asterisk version 1.0.9 and above.
Syntax:
These are the three possible ways to use this command(application).
List with the possible options
Purpose and usage
2. Screenshots of what you can see on your Idefisk and on the CLI of the Asterisk PBX
3. Additional information
4. Uploaded files
NOTE: This application is valid for Asterisk version 1.0.9 and above.
Syntax:
Authenticate(password[|options]) ;write the password in plain text
Authenticate(/passwordfile|[|options]) ;the character "/" means that the program will accept the argument as a name of file which has to contain a list of passwords.
Authenticate(/dbfamily/key|d) ; the password will be stored in the database
Authenticate(/passwordfile|[|options]) ;the character "/" means that the program will accept the argument as a name of file which has to contain a list of passwords.
Authenticate(/dbfamily/key|d) ; the password will be stored in the database
These are the three possible ways to use this command(application).
List with the possible options
a - this one will set a code to the password. The variable ${ACCOUNTCODE} will be set
d - Interpret path as database key family
r - This can be used only with the "d" option. It removes the database key after a successful entry.
j - If the authentication fails this one will set the priority to n+101 if there is such priority
d - Interpret path as database key family
r - This can be used only with the "d" option. It removes the database key after a successful entry.
j - If the authentication fails this one will set the priority to n+101 if there is such priority
Purpose and usage
So what is the purpose of this application and what can you use it for?
The purpose is obvious. This application gives you the opportunity to restrict the access to your telephone system.
You can use this command for many things.
For example: letís say that you want to make an IVR menu. With the help of Authenticate you can make private sections in it. The free part of the menu could contain messages about your new promotions and services. Then the access to the private parts will need an authentication code. For example the sections where you can check your bill or inquire invoice could be payable
Another example: You can restrict the access to the outside telephone system. So the employees from the lower levels can make calls only into the frames of the internal telephone line. However the managers of the company have to make calls to the outside telephone system.
The purpose is obvious. This application gives you the opportunity to restrict the access to your telephone system.
You can use this command for many things.
For example: letís say that you want to make an IVR menu. With the help of Authenticate you can make private sections in it. The free part of the menu could contain messages about your new promotions and services. Then the access to the private parts will need an authentication code. For example the sections where you can check your bill or inquire invoice could be payable
Another example: You can restrict the access to the outside telephone system. So the employees from the lower levels can make calls only into the frames of the internal telephone line. However the managers of the company have to make calls to the outside telephone system.
Prerequisites
To use this application you need a working Asterisk PBX with registered users in iax.conf, sip.conf or mgcp.conf(It depends on which protocol you would like to use) and made extensions.
To see how the application works we recommend to use our IAX softphone Idefisk. You can download it from here. Please also read our tutorial to learn how to configure it to work with Asterisk PBX.
To see how the application works we recommend to use our IAX softphone Idefisk. You can download it from here. Please also read our tutorial to learn how to configure it to work with Asterisk PBX.
Example of an IVR menu with the usage of Authenticate application
Below I am giving you screenshots of the iax.conf and extensions.conf files.
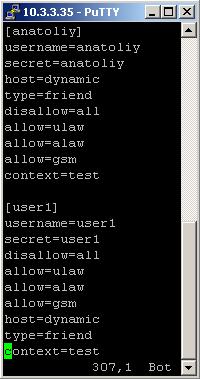
We have registered two users in the iax.conf - anatoliy and user1 with secret - anatoliy and user1. Type=friend means that this user can make and receive calls. Host=dynamic means that the IP is not static but dynamic through a DHCP server. Context=test - this shows that this user is working with the extensions in this context of the configuration file extensions.conf. Disallow=all means that this user does not support any audio codecs. However the next three lines allow=gsm, =alaw and =ulaw will turn on the support of these three codecs.
We have registered two users in the iax.conf - anatoliy and user1 with secret - anatoliy and user1. Type=friend means that this user can make and receive calls. Host=dynamic means that the IP is not static but dynamic through a DHCP server. Context=test - this shows that this user is working with the extensions in this context of the configuration file extensions.conf. Disallow=all means that this user does not support any audio codecs. However the next three lines allow=gsm, =alaw and =ulaw will turn on the support of these three codecs.

The configurations in extensions.conf are more interesting.
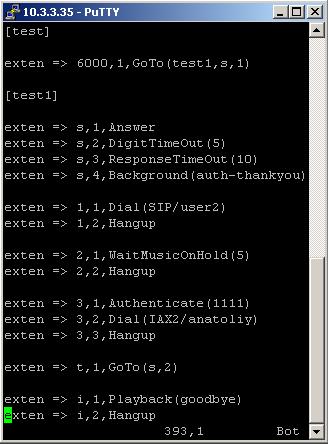
Firstly we have to make the context [test] with only one extension. When somebody dials 6000 this extension will transfer his call to the first extension of the next context [test1].
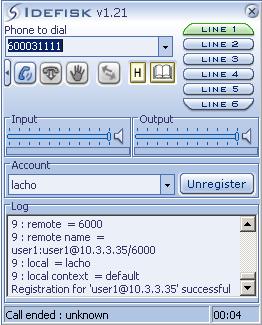
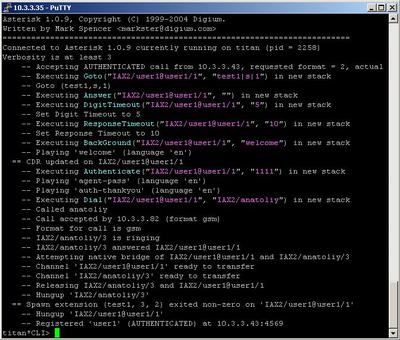
Secondly we have to make the extensions in the context [test1]. Letís take a close look at them. The first extension says to Asterisk PBX to answer the call. Then a welcome message will be played. The message will tell the caller that if he/she dials 1, he/she will be connected to the user user2, if he /she dials 2, will hear a music and if he/she dials 3, the call will be transfer to the private section of the IVR menu, where an authentication is required. If you write the password correctly you can go forward and you will be connected to the user anatoliy through IAX protocol.
Finally, as you can see the last two extensions contain t and i. These are predefined extension names. t is for timeout and i is for invalid. For more information about predefined extension names you can check here.
So in case of timeout your call will be transferred at the beginning of the context. In case of invalid operation you will hear a goodbye sound and the Asterisk PBX will hang up the line.
Firstly we have to make the context [test] with only one extension. When somebody dials 6000 this extension will transfer his call to the first extension of the next context [test1].
Secondly we have to make the extensions in the context [test1]. Letís take a close look at them. The first extension says to Asterisk PBX to answer the call. Then a welcome message will be played. The message will tell the caller that if he/she dials 1, he/she will be connected to the user user2, if he /she dials 2, will hear a music and if he/she dials 3, the call will be transfer to the private section of the IVR menu, where an authentication is required. If you write the password correctly you can go forward and you will be connected to the user anatoliy through IAX protocol.
Finally, as you can see the last two extensions contain t and i. These are predefined extension names. t is for timeout and i is for invalid. For more information about predefined extension names you can check here.
So in case of timeout your call will be transferred at the beginning of the context. In case of invalid operation you will hear a goodbye sound and the Asterisk PBX will hang up the line.

2. Screenshots of what you can see on your Idefisk and on the CLI of the Asterisk PBX
3. Additional information
For more information about extensions.conf you can check here.
For more information about iax.conf you can check here.
This application is tested with our IAX softphone Idefisk. You can download it from here. For more information about this softphone please read our tutorial.
If you would like to test this application with the SIP channel you can read our tutorials about the SIP Softphones to learn how to configure them to work with Asterisk PBX
For more information about iax.conf you can check here.
This application is tested with our IAX softphone Idefisk. You can download it from here. For more information about this softphone please read our tutorial.
If you would like to test this application with the SIP channel you can read our tutorials about the SIP Softphones to learn how to configure them to work with Asterisk PBX
4. Uploaded files
| Add Comment |
Latest Headlines:
-
T.38 faxing with Zoiper 2.15 is now easier than ever
section: voip software
-
Asterisk 1.4.21 Released
section: Asterisk
-
Asterisk 1.4.20 Released
section: Asterisk
-
Asterisk 1.4.20-rc2 Released
section: Asterisk
-
Asterisk 1.4.20-rc1 Now Available
section: Asterisk
- News Archives (older news)
Latest Tutorials:
-
Sending Fax from Zoiper to Zoiper using T.38
added 08/Dec/2008 18:16
-
VMAuthenticate (dialplan application)
added 01/Mar/2008 15:57
-
Siptronic ST-530
added 06/Nov/2007 17:57
-
Siemens C455 IP hardphone
added 05/Nov/2007 10:24
-
Zoiper
added 22/Oct/2007 17:53
Latest Comments:
-
https://tlajomulco.gob.mx/sites/default/...
tutorial: RemoveQueueMember (dialplan application)
-
OFFICIAL FACEBOOKS@:-
https://www.face...
tutorial: SIP with NAT or Firewalls
-
https://dcks-videahu.readme.io/
https:/...
tutorial: Installation of Asterisk GUI
-
https://zyo.se/one-piece-temporada-2
ht...
tutorial: Read (dialplan application)
-
https://bunny-wp-pullzone-ntwspdfrgr.b-c...
tutorial: SIP with NAT or Firewalls